-
Type:
Enhancement
-
Resolution: Fixed
-
Priority:
 P4
P4
-
Affects Version/s: None
-
Component/s: security-libs
-
b79
-
generic
-
generic
| Issue | Fix Version | Assignee | Priority | Status | Resolution | Resolved In Build |
|---|---|---|---|---|---|---|
| JDK-8135851 | emb-9 | Weijun Wang | P4 | Resolved | Fixed | team |
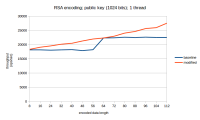
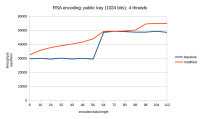
Currently sun.security.rsa.RSAPadding::padV15 uses fixed size (64 bytes) buffer for obtaining random bytes from SecureRandom.
Here we got two sources of inefficiency:
- when length of required padding is greater than 64 -> several calls of SecureRandom.nextBytes are required that increases contention blocking on SecureRandom
- when length of required padding is less than 64 it causes unnecessary overhead (e.g. nextBytes for 16 bytes is 4x times faster than for 64 bytes)
Suggested performance improvement shows RSA encoding speedup:
- 10%-18% when NativePRNG SecureRandom is used,
- 5%-7% when SHA1PRNG is used.
Here we got two sources of inefficiency:
- when length of required padding is greater than 64 -> several calls of SecureRandom.nextBytes are required that increases contention blocking on SecureRandom
- when length of required padding is less than 64 it causes unnecessary overhead (e.g. nextBytes for 16 bytes is 4x times faster than for 64 bytes)
Suggested performance improvement shows RSA encoding speedup:
- 10%-18% when NativePRNG SecureRandom is used,
- 5%-7% when SHA1PRNG is used.
- backported by
-
JDK-8135851 Ineffective SecureRandom usage in RSA encoding with PKCS1Padding.
-

- Resolved
-